One of Windows 10's most noticeable changes is the integration of Microsoft's new "Modern" or "Universal" apps. They're intended to offer a new method of delivering and creating applications that sit right alongside your old, familiar desktop applications. The idea is that Modern Apps offer a unified experience across desktop, laptop, phone and console - assuming you use Windows on your PCs, Windows Phone on your phone, and XBox on your console. At the same time, they give a single API core layer for development and a single distribution point through the Windows Store (or Windows Store for Business, when it arrives). So if you're sucking up the Microsoft kool-aid, it all sounds good, no?
Unfortunately there are a few problems with this.
Firstly, most of us have vast swathes of "legacy" desktop applications that we need to deliver to our users, and the primary need is to provision access to these. Modern Apps simply aren't popular enough at the moment to warrant our attention.
Secondly, some of the Modern Apps are quite good at clashing with our desktop application estates. OneNote, for instance, arrives as both a Modern App and also as part of the wider Office suite, and it can be confusing for the users to see both.
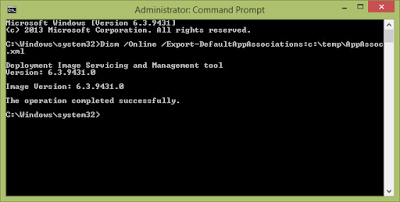
Thirdly, Modern Apps are quite good at aggressively resetting file type associations. If you've used Windows 10 for any length of time, there's a good chance you've seen a pop-up message like this
It's not just limited to things like AVI files - one of the most annoying is when it decides to reset your PDF association to Edge, or JPG association to Pictures. There is a Registry hack to get around this - see this article - but I'd sooner do something more permanent.
Fourth, there are some really weird apps in the Modern Apps list that I'd rather not see. Contact Support is the worst - my users are constantly thinking it is a way to get help from the IT department, but it's not. Microsoft missed a trick here by not making this application customizable, so I just want to get rid of it. They also made Calculator one of the Modern Apps, so if we can find a way to get rid of some, that's also one we want to keep!
Now, you can get around this problem of Modern Apps - mostly - by running your Windows 10 systems on the Long-Term Servicing Branch (LTSB). However, this puts you on what is essentially a different operating system that doesn't get feature upgrades (and therefore looks pretty dated very quickly). It's also something Microsoft would rather you didn't use, and besides, the Contact Support app I mentioned earlier still appears even though everything else - even Edge - is removed. I'd much rather be able to run on the Current Branch for Business (CBB) servicing branch, and just get rid of the Modern Apps.
Of course, some are probably saying, there are PowerShell cmdlets that let you remove Modern Apps from the base OS, aren't there? This is true. You can use the following command
Remove-AppXProvisionedPackage-Online-PackageName xxxx
where xxxx is the package name you want to remove. However, there are some limitations with this. Certain Modern Apps are listed as "part of the operating system" and cannot be removed. This is really annoying when, for instance, you might want to remove Microsoft Edge or the Contact Support app. It's also even more annoying when you realize that they've managed to remove Edge in LTSB but you can't do it in CBB in this fashion.
So how do we do it? We just want a CBB version of Windows 10 we can deploy without most of the useless and confusing Modern Apps. How difficult can that be?
In order to facilitate this, we need to understand how Windows 10 actually provisions a user's access to these Modern Apps.
You may have noticed, either if you're a Windows 10 user or a reader of this blog, that Windows 10 has a big logon delay when you first sign in. Most of this process is taken up by the creation of the Start Menu, the Start Tiles and the Modern Apps. The Start Menu isn't a filesystem any more like it was in Windows 7 and earlier. It's partly a filesystem - the "legacy" applications on the Start Menu are still pulled in from %PROGRAMDATA%\Microsoft\Windows\Start Menu\Programs - but the Modern App shortcuts are created on-the-fly at the user's first logon. This is also the reason that it's very difficult to roam the Start Menu or the Start Tiles or indeed many of the Modern App settings (Modern App settings are something for a later article) - they are compiled and expanded and tied up in a set of databases which make them very different from the way we're used to managing these things.
How do we stop this expansion/creation from happening, and also from being so intensive?
First we need to understand how it works under the hood.
When a user logs in to Windows 10 for the first time, the operating system looks in a few different places to get the information it needs to compile the Start Menu and the Start Tiles. Not all of them are listed here, but the main ones are:-
%WINDIR%\SystemApps
%PROGRAMFILES%\WindowsApps
These two folders are combined and dump out the user's version of all the associated apps to %LOCALAPPDATA%\Packages and other parts of the user's profile.
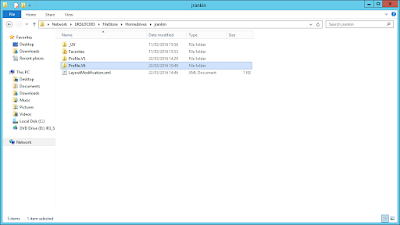
The SystemApps folder contains those Modern Apps that can't be removed via PowerShell. These include things like Contact Support and Edge. This folder can be accessed through Explorer:-
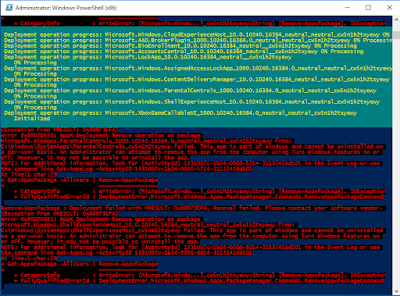
The WindowsApps folder, conversely, can't be accessed unless you take ownership of the folder and then modify the NTFS permissions. DON'T do this, though, as the very act of even slightly modifying the permissions on this folder stops ALL of your Modern Apps from working. With the benefit of snapshots and VMs, I have a screenshot of some of the folder contents below:-
This isn't all of them - there are 80+ Modern App folders here, which coupled with those from SystemApps, start to give you an idea of why a Windows 10 first logon takes so long. Given that Server 2016 looks like it will work with the same underlying operating system principles, I can only imagine that XenApp server logons are about to become horrendous in the extreme, as soon as a supported XenApp version for Server 2016 makes it out of the door.
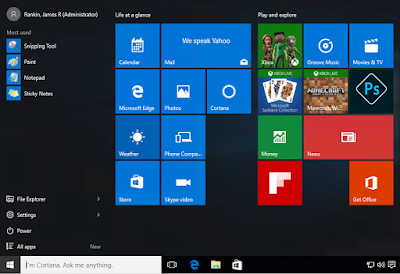
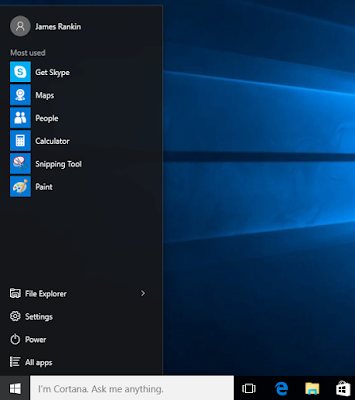
Once this process is completed, this is what gives you your default Windows Start Menu and Tiles as seen below
I can't speak for everyone, but the consumer focus of this default Menu, coupled with the patronising names for the groups - "Play and explore"...gimme a break - makes me cringe every time. The time the user has waited for all this stuff to be created that they probably won't even use winds me up even more.
The trick to disabling most of these Modern Apps is simply to rename the folders that they expand from. What we're going to do is prefix the apps folders we don't want with BLOCKED_, which means that we can easily revert the changes we make in the event there's an issue.
For the folders in %WINDIR%\SystemApps, this is fairly straightforward, because we can see them through the GUI. Log on as an administrator and run the following commands (lines may wrap):-
c:
cd "Windows\SystemApps"
ren ContactSupport_cw5n1h2txyewy BLOCKED_ContactSupport_cw5n1h2txyewy
ren Microsoft.MicrosoftEdge_8wekyb3d8bbwe BLOCKED_Microsoft.MicrosoftEdge_8wekyb3d8bbwe
ren Microsoft.XboxGameCallableUI_cw5n1h2txyewy BLOCKED_Microsoft.XboxGameCallableUI_cw5n1h2txyewy
ren Microsoft.XboxIdentityProvider_cw5n1h2txyewy BLOCKED_Microsoft.XboxIdentityProvider_cw5n1h2txyewy
ren WindowsFeedback_cw5n1h2txyewy BLOCKED_WindowsFeedback_cw5n1h2txyewy
This is cut down to just remove the Windows Feedback, XBox, Contact Support and Edge applications. If you want to keep some (like Edge), or disable some more of the system-level apps, simply add or remove lines as appropriate, inserting the folder names that you can view in Explorer.
Now, doing the same for the WindowsApps folder is a deal more tricky. For starters, you can't even see what's in it, even if you're logged on as an admin.
What you can do is download psexec.exe (part of the PSTools suite from Microsoft) and use it to run a command prompt as SYSTEM. Simply fire up a command prompt as an administrator and run the following command (assuming psexec is accessible):-
psexec -i -s cmd.exe
You should now have a command window that is running with SYSTEM privileges. From here, you can list the directories in c:\Program Files\WindowsApps without any issue.
As of today (April 18 2016), this was the list of folders in this directory:-
9E2F88E3.Twitter_5.0.1.0_x86__wgeqdkkx372wm
king.com.CandyCrushSodaSaga_1.62.900.0_x86__kgqvnymyfvs32
Microsoft.3DBuilder_10.9.50.0_neutral_~_8wekyb3d8bbwe
Microsoft.3DBuilder_10.9.50.0_x64__8wekyb3d8bbwe
Microsoft.Appconnector_1.3.3.0_neutral__8wekyb3d8bbwe
Microsoft.Appconnector_2015.707.550.0_neutral_~_8wekyb3d8bbwe
Microsoft.BingFinance_4.6.169.0_neutral_~_8wekyb3d8bbwe
Microsoft.BingFinance_4.6.169.0_x86__8wekyb3d8bbwe
Microsoft.BingNews_4.6.169.0_neutral_~_8wekyb3d8bbwe
Microsoft.BingNews_4.6.169.0_x86__8wekyb3d8bbwe
Microsoft.BingSports_4.6.169.0_neutral_~_8wekyb3d8bbwe
Microsoft.BingSports_4.6.169.0_x86__8wekyb3d8bbwe
Microsoft.BingWeather_4.6.169.0_neutral_~_8wekyb3d8bbwe
Microsoft.BingWeather_4.6.169.0_x86__8wekyb3d8bbwe
Microsoft.CommsPhone_1.10.15000.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.CommsPhone_1.10.15000.0_neutral_~_8wekyb3d8bbwe
Microsoft.CommsPhone_1.10.15000.0_x64__8wekyb3d8bbwe
Microsoft.ConnectivityStore_1.1509.1.0_neutral_~_8wekyb3d8bbwe
Microsoft.ConnectivityStore_1.1509.1.0_x64__8wekyb3d8bbwe
Microsoft.Getstarted_2.3.7.0_neutral_~_8wekyb3d8bbwe
Microsoft.Getstarted_2.3.7.0_x64__8wekyb3d8bbwe
Microsoft.Messaging_1.10.22012.0_neutral_split.scale-150_8wekyb3d8bbwe
Microsoft.Messaging_1.10.22012.0_neutral_~_8wekyb3d8bbwe
Microsoft.Messaging_1.10.22012.0_x86__8wekyb3d8bbwe
Microsoft.MicrosoftOfficeHub_17.6306.23501.0_x64__8wekyb3d8bbwe
Microsoft.MicrosoftOfficeHub_2015.6306.23501.0_neutral_~_8wekyb3d8bbwe
Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_neutral_~_8wekyb3d8bbwe
Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_x64__8wekyb3d8bbwe
Microsoft.NET.Native.Framework.1.0_1.0.22929.0_x64__8wekyb3d8bbwe
Microsoft.NET.Native.Framework.1.0_1.0.22929.0_x86__8wekyb3d8bbwe
Microsoft.NET.Native.Framework.1.1_1.0.23115.0_x64__8wekyb3d8bbwe
Microsoft.NET.Native.Framework.1.1_1.0.23115.0_x86__8wekyb3d8bbwe
Microsoft.NET.Native.Framework.1.2_1.2.23231.0_x64__8wekyb3d8bbwe
Microsoft.NET.Native.Framework.1.2_1.2.23231.0_x86__8wekyb3d8bbwe
Microsoft.NET.Native.Runtime.1.0_1.0.22929.0_x64__8wekyb3d8bbwe
Microsoft.NET.Native.Runtime.1.0_1.0.22929.0_x86__8wekyb3d8bbwe
Microsoft.NET.Native.Runtime.1.1_1.1.23118.0_x64__8wekyb3d8bbwe
Microsoft.NET.Native.Runtime.1.1_1.1.23118.0_x86__8wekyb3d8bbwe
Microsoft.NET.Native.Runtime.1.1_1.1.23406.0_x64__8wekyb3d8bbwe
Microsoft.NET.Native.Runtime.1.1_1.1.23406.0_x86__8wekyb3d8bbwe
Microsoft.Office.OneNote_17.6131.10051.0_x64__8wekyb3d8bbwe
Microsoft.Office.OneNote_2015.6131.10051.0_neutral_~_8wekyb3d8bbwe
Microsoft.Office.Sway_17.6216.20251.0_x64__8wekyb3d8bbwe
Microsoft.Office.Sway_2015.6216.20251.0_neutral_~_8wekyb3d8bbwe
Microsoft.People_10.0.2840.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.People_10.0.2840.0_x64__8wekyb3d8bbwe
Microsoft.People_2015.1012.106.0_neutral_~_8wekyb3d8bbwe
Microsoft.SkypeApp_3.2.1.0_neutral_~_kzf8qxf38zg5c
Microsoft.SkypeApp_3.2.1.0_x86__kzf8qxf38zg5c
Microsoft.VCLibs.120.00_12.0.21005.1_x64__8wekyb3d8bbwe
Microsoft.VCLibs.120.00_12.0.21005.1_x86__8wekyb3d8bbwe
Microsoft.VCLibs.140.00_14.0.22929.0_x64__8wekyb3d8bbwe
Microsoft.VCLibs.140.00_14.0.22929.0_x86__8wekyb3d8bbwe
Microsoft.VCLibs.140.00_14.0.23816.0_x64__8wekyb3d8bbwe
Microsoft.VCLibs.140.00_14.0.23816.0_x86__8wekyb3d8bbwe
Microsoft.Windows.Photos_15.1001.16470.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.Windows.Photos_15.1001.16470.0_x64__8wekyb3d8bbwe
Microsoft.Windows.Photos_2015.1001.17200.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsAlarms_10.1510.12020.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.WindowsAlarms_10.1510.12020.0_x64__8wekyb3d8bbwe
Microsoft.WindowsAlarms_2015.1012.20.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsCalculator_10.1510.9020.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.WindowsCalculator_10.1510.9020.0_x64__8wekyb3d8bbwe
Microsoft.WindowsCalculator_2015.1009.20.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsCamera_2015.1071.40.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.WindowsCamera_2015.1071.40.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsCamera_2015.1071.40.0_x64__8wekyb3d8bbwe
microsoft.windowscommunicationsapps_17.6308.42271.0_x64__8wekyb3d8bbwe
microsoft.windowscommunicationsapps_2015.6308.42271.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsMaps_4.1509.50911.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.WindowsMaps_4.1509.50911.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsMaps_4.1509.50911.0_x64__8wekyb3d8bbwe
Microsoft.WindowsPhone_10.1510.9010.0_x64__8wekyb3d8bbwe
Microsoft.WindowsPhone_2015.1009.10.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsSoundRecorder_10.1510.12110.0_x64__8wekyb3d8bbwe
Microsoft.WindowsSoundRecorder_2015.1012.110.0_neutral_~_8wekyb3d8bbwe
Microsoft.WindowsStore_2015.10.13.0_neutral_split.scale-100_8wekyb3d8bbwe
Microsoft.WindowsStore_2015.10.13.0_x64__8wekyb3d8bbwe
Microsoft.WindowsStore_2015.1013.14.0_neutral_~_8wekyb3d8bbwe
Microsoft.XboxApp_2015.930.526.0_neutral_~_8wekyb3d8bbwe
Microsoft.XboxApp_9.9.30030.0_x64__8wekyb3d8bbwe
Microsoft.ZuneMusic_2019.6.13251.0_neutral_~_8wekyb3d8bbwe
Microsoft.ZuneMusic_3.6.13251.0_neutral_resources.scale-140_8wekyb3d8bbwe
Microsoft.ZuneMusic_3.6.13251.0_x64__8wekyb3d8bbwe
Microsoft.ZuneVideo_2019.6.13251.0_neutral_~_8wekyb3d8bbwe
Microsoft.ZuneVideo_3.6.13251.0_neutral_resources.scale-150_8wekyb3d8bbwe
Microsoft.ZuneVideo_3.6.13251.0_x64__8wekyb3d8bbwe
This may change as new updates are applied to Windows 10, so you may need to run the command prompt as SYSTEM and export the listing of a dir command out to a text file to see if the following rename commands need to be added to.
But for now, I identified the Modern Apps in this list that I wanted rid of and added them to another simple batch command. I have commented out the ones I wanted to keep with the :: notation. Again, you can customize this list as you require, depending on what you would like to keep or get rid of (again, lines may have wrapped). Don't forget to test thoroughly first though!
c:
cd "Program Files\WindowsApps"
ren 9E2F88E3.Twitter_5.0.1.0_x86__wgeqdkkx372wm BLOCKED_9E2F88E3.Twitter_5.0.1.0_x86__wgeqdkkx372wm
ren king.com.CandyCrushSodaSaga_1.62.900.0_x86__kgqvnymyfvs32 BLOCKED_king.com.CandyCrushSodaSaga_1.62.900.0_x86__kgqvnymyfvs32
ren Microsoft.3DBuilder_10.9.50.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.3DBuilder_10.9.50.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.3DBuilder_10.9.50.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.3DBuilder_10.9.50.0_x64__8wekyb3d8bbwe
:: ren Microsoft.Appconnector_1.3.3.0_neutral__8wekyb3d8bbwe BLOCKED_Microsoft.Appconnector_1.3.3.0_neutral__8wekyb3d8bbwe
:: ren Microsoft.Appconnector_2015.707.550.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.Appconnector_2015.707.550.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.BingFinance_4.6.169.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.BingFinance_4.6.169.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.BingFinance_4.6.169.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.BingFinance_4.6.169.0_x86__8wekyb3d8bbwe
ren Microsoft.BingNews_4.6.169.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.BingNews_4.6.169.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.BingNews_4.6.169.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.BingNews_4.6.169.0_x86__8wekyb3d8bbwe
ren Microsoft.BingSports_4.6.169.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.BingSports_4.6.169.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.BingSports_4.6.169.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.BingSports_4.6.169.0_x86__8wekyb3d8bbwe
ren Microsoft.BingWeather_4.6.169.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.BingWeather_4.6.169.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.BingWeather_4.6.169.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.BingWeather_4.6.169.0_x86__8wekyb3d8bbwe
:: ren Microsoft.CommsPhone_1.10.15000.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.CommsPhone_1.10.15000.0_neutral_split.scale-100_8wekyb3d8bbwe
:: ren Microsoft.CommsPhone_1.10.15000.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.CommsPhone_1.10.15000.0_neutral_~_8wekyb3d8bbwe
:: ren Microsoft.CommsPhone_1.10.15000.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.CommsPhone_1.10.15000.0_x64__8wekyb3d8bbwe
:: ren Microsoft.ConnectivityStore_1.1509.1.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.ConnectivityStore_1.1509.1.0_neutral_~_8wekyb3d8bbwe
:: ren Microsoft.ConnectivityStore_1.1509.1.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.ConnectivityStore_1.1509.1.0_x64__8wekyb3d8bbwe
ren Microsoft.Getstarted_2.3.7.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.Getstarted_2.3.7.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.Getstarted_2.3.7.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.Getstarted_2.3.7.0_x64__8wekyb3d8bbwe
ren Microsoft.Messaging_1.10.22012.0_neutral_split.scale-150_8wekyb3d8bbwe BLOCKED_Microsoft.Messaging_1.10.22012.0_neutral_split.scale-150_8wekyb3d8bbwe
ren Microsoft.Messaging_1.10.22012.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.Messaging_1.10.22012.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.Messaging_1.10.22012.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.Messaging_1.10.22012.0_x86__8wekyb3d8bbwe
ren Microsoft.MicrosoftOfficeHub_17.6306.23501.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.MicrosoftOfficeHub_17.6306.23501.0_x64__8wekyb3d8bbwe
ren Microsoft.MicrosoftOfficeHub_2015.6306.23501.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.MicrosoftOfficeHub_2015.6306.23501.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_neutral_split.scale-100_8wekyb3d8bbwe
ren Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.MicrosoftSolitaireCollection_3.3.9211.0_x64__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Framework.1.0_1.0.22929.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Framework.1.0_1.0.22929.0_x64__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Framework.1.0_1.0.22929.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Framework.1.0_1.0.22929.0_x86__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Framework.1.1_1.0.23115.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Framework.1.1_1.0.23115.0_x64__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Framework.1.1_1.0.23115.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Framework.1.1_1.0.23115.0_x86__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Framework.1.2_1.2.23231.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Framework.1.2_1.2.23231.0_x64__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Framework.1.2_1.2.23231.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Framework.1.2_1.2.23231.0_x86__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Runtime.1.0_1.0.22929.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Runtime.1.0_1.0.22929.0_x64__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Runtime.1.0_1.0.22929.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Runtime.1.0_1.0.22929.0_x86__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Runtime.1.1_1.1.23118.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Runtime.1.1_1.1.23118.0_x64__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Runtime.1.1_1.1.23118.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Runtime.1.1_1.1.23118.0_x86__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Runtime.1.1_1.1.23406.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Runtime.1.1_1.1.23406.0_x64__8wekyb3d8bbwe
:: ren Microsoft.NET.Native.Runtime.1.1_1.1.23406.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.NET.Native.Runtime.1.1_1.1.23406.0_x86__8wekyb3d8bbwe
ren Microsoft.Office.OneNote_17.6131.10051.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.Office.OneNote_17.6131.10051.0_x64__8wekyb3d8bbwe
ren Microsoft.Office.OneNote_2015.6131.10051.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.Office.OneNote_2015.6131.10051.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.Office.Sway_17.6216.20251.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.Office.Sway_17.6216.20251.0_x64__8wekyb3d8bbwe
ren Microsoft.Office.Sway_2015.6216.20251.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.Office.Sway_2015.6216.20251.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.People_10.0.2840.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.People_10.0.2840.0_neutral_split.scale-100_8wekyb3d8bbwe
ren Microsoft.People_10.0.2840.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.People_10.0.2840.0_x64__8wekyb3d8bbwe
ren Microsoft.People_2015.1012.106.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.People_2015.1012.106.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.SkypeApp_3.2.1.0_neutral_~_kzf8qxf38zg5c BLOCKED_Microsoft.SkypeApp_3.2.1.0_neutral_~_kzf8qxf38zg5c
ren Microsoft.SkypeApp_3.2.1.0_x86__kzf8qxf38zg5c BLOCKED_Microsoft.SkypeApp_3.2.1.0_x86__kzf8qxf38zg5c
:: ren Microsoft.VCLibs.120.00_12.0.21005.1_x64__8wekyb3d8bbwe BLOCKED_Microsoft.VCLibs.120.00_12.0.21005.1_x64__8wekyb3d8bbwe
:: ren Microsoft.VCLibs.120.00_12.0.21005.1_x86__8wekyb3d8bbwe BLOCKED_Microsoft.VCLibs.120.00_12.0.21005.1_x86__8wekyb3d8bbwe
:: ren Microsoft.VCLibs.140.00_14.0.22929.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.VCLibs.140.00_14.0.22929.0_x64__8wekyb3d8bbwe
:: ren Microsoft.VCLibs.140.00_14.0.22929.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.VCLibs.140.00_14.0.22929.0_x86__8wekyb3d8bbwe
:: ren Microsoft.VCLibs.140.00_14.0.23816.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.VCLibs.140.00_14.0.23816.0_x64__8wekyb3d8bbwe
:: ren Microsoft.VCLibs.140.00_14.0.23816.0_x86__8wekyb3d8bbwe BLOCKED_Microsoft.VCLibs.140.00_14.0.23816.0_x86__8wekyb3d8bbwe
ren Microsoft.Windows.Photos_15.1001.16470.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.Windows.Photos_15.1001.16470.0_neutral_split.scale-100_8wekyb3d8bbwe
ren Microsoft.Windows.Photos_15.1001.16470.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.Windows.Photos_15.1001.16470.0_x64__8wekyb3d8bbwe
ren Microsoft.Windows.Photos_2015.1001.17200.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.Windows.Photos_2015.1001.17200.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.WindowsAlarms_10.1510.12020.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsAlarms_10.1510.12020.0_neutral_split.scale-100_8wekyb3d8bbwe
ren Microsoft.WindowsAlarms_10.1510.12020.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.WindowsAlarms_10.1510.12020.0_x64__8wekyb3d8bbwe
ren Microsoft.WindowsAlarms_2015.1012.20.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsAlarms_2015.1012.20.0_neutral_~_8wekyb3d8bbwe
:: ren Microsoft.WindowsCalculator_10.1510.9020.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsCalculator_10.1510.9020.0_neutral_split.scale-100_8wekyb3d8bbwe
:: ren Microsoft.WindowsCalculator_10.1510.9020.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.WindowsCalculator_10.1510.9020.0_x64__8wekyb3d8bbwe
ren Microsoft.WindowsCalculator_2015.1009.20.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsCalculator_2015.1009.20.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.WindowsCamera_2015.1071.40.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsCamera_2015.1071.40.0_neutral_split.scale-100_8wekyb3d8bbwe
ren Microsoft.WindowsCamera_2015.1071.40.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsCamera_2015.1071.40.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.WindowsCamera_2015.1071.40.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.WindowsCamera_2015.1071.40.0_x64__8wekyb3d8bbwe
ren microsoft.windowscommunicationsapps_17.6308.42271.0_x64__8wekyb3d8bbwe BLOCKED_microsoft.windowscommunicationsapps_17.6308.42271.0_x64__8wekyb3d8bbwe
ren microsoft.windowscommunicationsapps_2015.6308.42271.0_neutral_~_8wekyb3d8bbwe BLOCKED_microsoft.windowscommunicationsapps_2015.6308.42271.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.WindowsMaps_4.1509.50911.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsMaps_4.1509.50911.0_neutral_split.scale-100_8wekyb3d8bbwe
ren Microsoft.WindowsMaps_4.1509.50911.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsMaps_4.1509.50911.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.WindowsMaps_4.1509.50911.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.WindowsMaps_4.1509.50911.0_x64__8wekyb3d8bbwe
ren Microsoft.WindowsPhone_10.1510.9010.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.WindowsPhone_10.1510.9010.0_x64__8wekyb3d8bbwe
ren Microsoft.WindowsPhone_2015.1009.10.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsPhone_2015.1009.10.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.WindowsSoundRecorder_10.1510.12110.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.WindowsSoundRecorder_10.1510.12110.0_x64__8wekyb3d8bbwe
ren Microsoft.WindowsSoundRecorder_2015.1012.110.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsSoundRecorder_2015.1012.110.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.WindowsStore_2015.10.13.0_neutral_split.scale-100_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsStore_2015.10.13.0_neutral_split.scale-100_8wekyb3d8bbwe
ren Microsoft.WindowsStore_2015.10.13.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.WindowsStore_2015.10.13.0_x64__8wekyb3d8bbwe
ren Microsoft.WindowsStore_2015.1013.14.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.WindowsStore_2015.1013.14.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.XboxApp_2015.930.526.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.XboxApp_2015.930.526.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.XboxApp_9.9.30030.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.XboxApp_9.9.30030.0_x64__8wekyb3d8bbwe
ren Microsoft.ZuneMusic_2019.6.13251.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.ZuneMusic_2019.6.13251.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.ZuneMusic_3.6.13251.0_neutral_resources.scale-140_8wekyb3d8bbwe BLOCKED_Microsoft.ZuneMusic_3.6.13251.0_neutral_resources.scale-140_8wekyb3d8bbwe
ren Microsoft.ZuneMusic_3.6.13251.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.ZuneMusic_3.6.13251.0_x64__8wekyb3d8bbwe
ren Microsoft.ZuneVideo_2019.6.13251.0_neutral_~_8wekyb3d8bbwe BLOCKED_Microsoft.ZuneVideo_2019.6.13251.0_neutral_~_8wekyb3d8bbwe
ren Microsoft.ZuneVideo_3.6.13251.0_neutral_resources.scale-150_8wekyb3d8bbwe BLOCKED_Microsoft.ZuneVideo_3.6.13251.0_neutral_resources.scale-150_8wekyb3d8bbwe
ren Microsoft.ZuneVideo_3.6.13251.0_x64__8wekyb3d8bbwe BLOCKED_Microsoft.ZuneVideo_3.6.13251.0_x64__8wekyb3d8bbwe
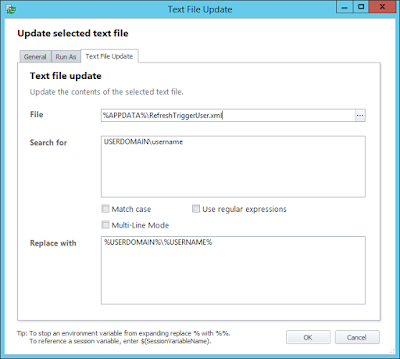
Now once you've done this, any user who logs on to the machine will see that the folders we have renamed to "BLOCKED_" get ignored when the Start Menu and Tiles are created, cutting down the logon time as well as making things much more slick and familiar for our users. However, what you may notice is that whereas the Start Menu is now nice and streamlined, the Start Tiles have still tried to set up all of the default shortcuts - they just couldn't find them, resulting in the unholy mess you see in the image below.
Clearly the Start Tiles also have a dependency on another file somewhere - can we find where it is?
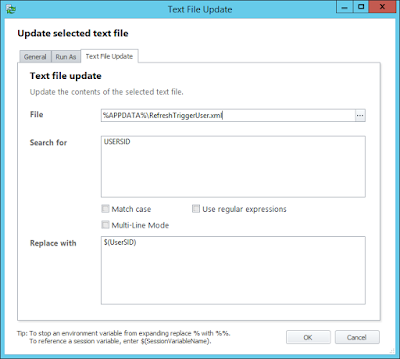
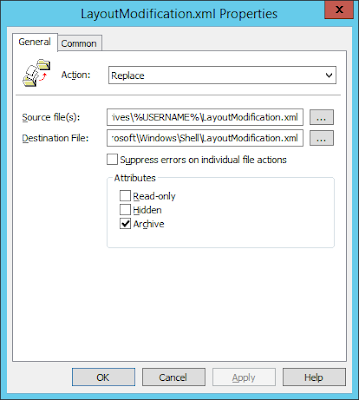
Of course we can :-) In the default user profile, specifically in C:\Users\Default\AppData\Local\Microsoft\Windows\Shell, there is a large (98KB) XML file called DefaultLayouts. This is the file that tells the operating system how to try and construct the default Start Tiles. If you delete this file and log on, your Start Menu will simply look like this:-
That looks vastly better already, but what if we used the technique we discussed in an earlier article for exporting the Start Tile layout in conjunction with this? So we simply remove the DefaultLayouts.xml file and drop in there a LayoutModification.xml file, as discussed in the previous article? In case you don't want to trawl the earlier article, here's a quick recap
- Log on to a Windows 10 endpoint and configure the Start Tiles as you want them to appear to the user
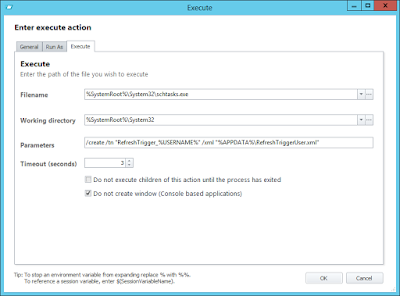
- Export this using the Export-StartLayout cmdlet to a file called LayoutModification.xml
- Copy this file into C:\Users\Default\AppData\Local\Microsoft\Windows\Shell in your image or endpoints
- Remove the DefaultLayouts.xml file from the same folder (actually, in testing, whether this file was present or not made no difference, so you can possibly omit this step and simply use the LayoutModification.xml file)
This actually seems to work really swimmingly. Check out my customized, streamlined Start Menu and Tiles, with a minimum of Modern Apps and no confusion for the user. You could trim this down even further still (no idea really why I actually left the Microsoft Wifi and Phone apps on there) - simply edit the commands from earlier in the article if you wish to try and make it leaner and meaner!
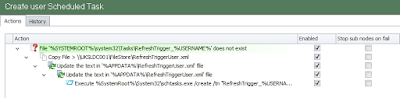
Deployment of this can be done in a number of ways. You can use scripts or tools to make these changes on your base operating system prior to users logging on, but perhaps the most efficient way would be to deliver these tweaks as part of the build process or even incorporate them into the base image (irrespective of the technology you're using to deliver it). The psexec requirement makes it slightly challenging, but a bit of scripting should suffice to allow you to change the folders in %PROGRAMFILES%\WindowsApps without touching the NTFS ACLs, which is a surefire way to break the Modern Apps entirely.
So there you have it - a method to give yourself Windows 10 machines on Current Branch for Business with the exact set of Modern Apps that you deem necessary (in my experience, quite a short list). Needless to say, Microsoft may shovel down updated versions of Modern Apps through the update channel that could possibly make some of them reappear, but if you keep a close eye on things, you should be able to intercept and disable these using the techniques described above.
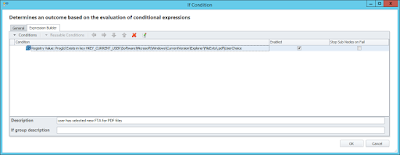
I shall be making a quick video of this method at some point - a link will be posted at the end of the article as soon as it is published on my YouTube channel. And a shout out to Charlie Barrett of SCC for pointing me in the right direction to unearth some of Windows 10's under-the-hood behaviour.Update 19/04/16I noticed late last night that Microsoft updated all of the Modern Apps on my test machines, which incremented all of the version numbers of the folders we talked about earlier. So I quickly knocked up a batch script which will rename all of the targetfolders no matter what the version number. Obviously, test thoroughly before using this or any of the techniques in this article. I've got enough problems fixing my own screw-ups to be held responsible for anyone else's! ;-)The commands will need to be saved as a .bat or .cmd file and executed with the SYSTEM privileges we described earlier, for which you will need to spawn a command window using psexec.exe (details given further up the page). I didn't have time to attack this in PowerShell - anyone wants to try it, feel free. I may revisit it later to convert it to PS.Obviously, as previously, I have put in the names of the folders that I have elected to remove (or keep, if they're not in the script!) Customize this as necessary for your environment.Here's the script:-@echo off
setlocal
setlocal enableextensions
:: Move to correct folder
c:
cd "\Program Files\WindowsApps"
:: Pull full names of target folders in WindowsApps, and pass to renaming routine
for /d %%a in ("C:\Program Files\WindowsApps\9E2F88E3.Twitter*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.Bing*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\king.com*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.3D*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.CommsPhone*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.GetStarted*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.Messaging*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.MicrosoftOfficeHub*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.MicrosoftSolitaire*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.Office*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.People*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.Skype*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.Windows.Photos*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.WindowsAlarms*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.WindowsCamera*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.windowscommunicationsapps*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.WindowsMaps*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.WindowsPhone*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.WindowsSoundRecorder*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.WindowsStore*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.Xbox*") do set fullsourcepath=%%a & CALL :RENAME
for /d %%a in ("C:\Program Files\WindowsApps\Microsoft.Zune*") do set fullsourcepath=%%a & CALL :RENAME
:: Rename target folders in SystemApps
cd "\Windows\SystemApps"
ren ContactSupport_cw5n1h2txyewy BLOCKED_ContactSupport_cw5n1h2txyewy
ren Microsoft.MicrosoftEdge_8wekyb3d8bbwe BLOCKED_Microsoft.MicrosoftEdge_8wekyb3d8bbwe
ren Microsoft.XboxGameCallableUI_cw5n1h2txyewy BLOCKED_Microsoft.XboxGameCallableUI_cw5n1h2txyewy
ren Microsoft.XboxIdentityProvider_cw5n1h2txyewy BLOCKED_Microsoft.XboxIdentityProvider_cw5n1h2txyewy
ren WindowsFeedback_cw5n1h2txyewy BLOCKED_WindowsFeedback_cw5n1h2txyewy
endlocal
goto :eof
:RENAME
:: Rename WindowsApps folders
Echo.
Echo Renaming folder %fullsourcepath%...
Echo.
:: Pull the folder name (minus full path) for destination
for /f "tokens=4 delims=\" %%b in ('echo %fullsourcepath%') do set fulldestpath=%%b
:: Rename folder to BLOCKED_xxxx
ren "%fullsourcepath%" BLOCKED_%fulldestpath%
goto :eof
I've tested this on a few Windows 10 machines, and it seems to work OK. I will be testing again when the next batch of Modern App updates sneak out (they don't appear to come through "ordinary" channels such as WSUS or SCCM).Update 21/04/2016In order to stop Modern Apps coming back down to your machine, you have a couple of choices. You could either run the script above on a schedule of some sort (you would have to call the script from psexec with the /accepteula switch, probably at startup or as a Scheduled Task), or you could disable Modern App updates by GPO.I prefer the second option, and this would be a good thing in general as Modern Apps update outside of the normal channels, and are quite good at suddenly shovelling down changes when Microsoft feel like it. Remember when Microsoft Sway suddenly appeared on everyone's Start Tiles, or when our Lock Screens decided they were going to show Rise of the Tomb Raider adverts instead of our corporate logo? This is not really acceptable in corporate environments, and if you were using Edge, for instance, and an overnight unscheduled update suddenly broke all your web apps, you'd be kind of miffed.The GPO is in Computer Config | Admin Templates | Windows Components | Store, and will need to be set from a Windows 10 or Server 2016 machine if you haven't got a central GPO ADMX share.Set "Turn off automatic download and install of updates" to kill the Modern App update mechanism, and you might want to add "Turn off the offer to update to the latest version of Windows" while you're in there.