Unless you've been living under a rock for the past year or so, I'm sure you've encountered the general hubbub about Windows 10 and how it uses advanced "telemetry" (one of the most wonderful euphemisms for "logging" or "monitoring" I've ever heard). Now we all know there's no such thing as a free lunch (unless you're at a Citrix User Group), and with Windows 10 being a free download, it was always to be expected that they'd use a tried-and-tested monetization model to make it worth their while to deliver a new operating system free of charge. Ever since I started my current deployment of Windows 10 (which is running across a mix of physical desktops and XenDesktop 7.6 thin clients), privacy, telemetry and compliance are words I've been hearing in focus meetings more and more often.
How you want to manage Windows 10's telemetry settings depends on a number of factors. What sort of industry you work in (those with strict compliance rules, like finance and healthcare, are particularly pertinent here), how users are managing their data (in-house or synchronized out to some form of cloud-based solution), and your general level of tinfoil-hattery.
I've found a number of methods to cut down on Windows 10's talkativeness and ability to contact the mother-ship, however many of these you utilize depends on just how insanely suspicious you are capable of being. Bear in mind, though, that cutting off some of these functions - particularly the ones in the "Batshit Paranoid" section - may prevent certain aspects of the Windows 10 operating system from functioning correctly, so as usual, a big amount of checking and testing is required. Microsoft are also quite capable of shovelling updates down your throats under the disguise of some innocuous blurb to reverse any mitigation you may put in place, and this sort of cloak-and-dagger routine is, in my humble opinion, the single worst facet of Windows 10 as an operating system. Understanding what updates are going to change is vital for home users as much as systems administrators, and I've found an increasing number of users who are switching off Windows 10 Automatic Updates in view of this, undoing over a decade's work from Microsoft which convinced users that updating automatically was a good idea. Increasing the attack surface of Internet-exposed machines is simply the last thing we want to be encouraging, yet here we are. More on my opinion around Windows 10 in general in an article later this week, hopefully.
I had to use AppSense for the tooling because of the requirement for a delay after logon before importing the settings, so traditional Group Policy/scripted methods will probably be unsuitable here, although the more skilled scripters among you should be able to adapt. Ideally, though, to enforce these privacy settings and save yourselves from having your policies overwritten by the default profile, a high-end UEM solution of some sort is required.
Spaying your Windows 10 instance
1. Universal Apps
First step is to ensure that your Windows 10 is as unintrusive as is humanly possible, by removing apps and features that you don't require.
Given how bad the feedback on Universal Apps has been so far, I'd be in the mood to remove all of them (except Edge maybe - my users seem happy about that, although given they're coming from IE7 most anything is an improvement). If you're on LTSB most of the Universal Apps are removed anyway, but any other servicing branch and you'll have all of the horrid guff hanging from your Start Menu. They also love to talk back to Microsoft!
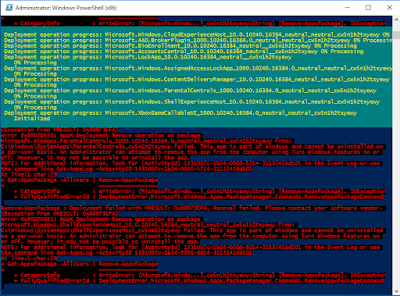
Get rid of most of these (with the exceptions of the annoying Contact Support and Windows Feedback) by getting down-and-dirty with this bit of handy PowerShell (you will need to run it with admin privileges)
and you should see something like this (you can ignore all of the errors - they're just stuff that, for whatever reason, can't be removed)
You can also use this command
if you want to remove applications in the image rather than after the operating system has been loaded.
Cortana should be removed as part of this process also.
2. Web search from desktop
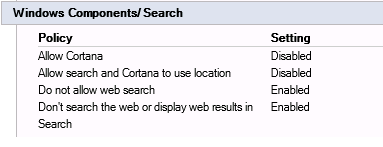
You can get rid of web search and avoid routing everything you search for through Bing by using some Group Policy Objects. Rather annoyingly (and not very surprisingly these days), they are computer GPOs rather than user ones. Configure the settings in Computer Configuration | Admin Templates | Windows Components | Search as below (these settings are included in my example configuration)
3. Telemetry
If you're using the Enterprise version of Windows 10, you can disable Telemetry through GPO as well. If you're not on Enterprise - well, you can reduce it somewhat, but not kill it. With this in mind, I'd recommend everyone use Enterprise where possible and setting the policy to Off(shown below - also included in the example configuration)
If you're not on Enterprise all you can do is go for Basic as the setting. The differences between Basic, Enhanced and Fullare known only to Microsoft (Off is supposed to send nothing at all, but I don't believe that for a second), but they do insinuate that Off or Basic will "degrade certain experiences on the device". It may well degrade the experience of being spied on and monitored, but I haven't noticed anything keel over and die since I deployed this to my users in Off mode.
Apparently (though I can't confirm), if you're not on Enterprise you can trick Windows into disabling telemetry by creating the following Registry value
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DataCollection
DWORD AllowTelemetry Value 0
although I'm fairly sure if this works, Microsoft will plug the hole as soon as possible.
4. Detailed privacy settings
At build time there's a bunch of stuff you can do to turn off most of the nosier features of Windows 10. You can also do this post-build, but controlling them centrally is a little more challenging. I've put together a set of policy objects and preferences (available in AppSense Environment Manager format), which will need to be imported onto a Windows 10 machine with a copy of the Windows 10 ADMX files running the required EM Console.
You will need to check and test these to ensure that they aren't conflicting with existing policies. A lot of them I've put in as Computer GPOs because they are restricted to that scope, but there may be a few available as User settings as well. The Registry values, for settings that don't have policies attached, are all set in the user context.
For the Contacts settings, the Registry key contains a SID - S-1-15-2-155514346-2573954481-755741238-1654018636-1233331829-3075935687-2861478708 - which does not resolve to anything on my test domain or test machines. You actually need to use this SID hard-coded as part of the Registry path to get the Contacts settings successfully blocked. Not sure where this has come from.
There is also a distressing tendency for the default profile creation to overwrite a lot of the Registry settings we have configured here (well, no-one said it was going to be easy!) To get around this, we will have to resurrect the Post-Logon Trigger that was supposed to be replaced by Desktop Created in AppSense (not the first time we've done this in the post-Windows 7 world), to import our settings in after Microsoft's default profile has done its damage. Big feature request to AppSense - give us a native "Delayed Trigger", customizable to a specific time frame after logon (Scense, one of your competitors, can do this natively), or even something like a "Refresh Trigger" (again, Scense has it) that runs at a pre-determined interval. Since Windows 8 and 10 came along the Desktop Created trigger runs too early to head off some of Microsoft's more questionable programming choices - please save us from using the PowerShell method and make it native in a new release!
The Environment Manager config is available here, and contains the necessary settings for the Post-Logon Trigger as well. What you will notice is there are some fabulous names for the Registry values we're using, and they make a little bit of a mockery of Microsoft's benign intentions for your data - HarvestContacts and RestrictImplicitTextCollection being my personal favourites.
You may actually need to tweak the delay in the Post-Logon Trigger dependent on your profile, I had to increase from 2000ms to 8000ms in one case. In the PowerShell that creates the .cs file (see the attached config), increase the sleep timeout as necessary to get it to work.
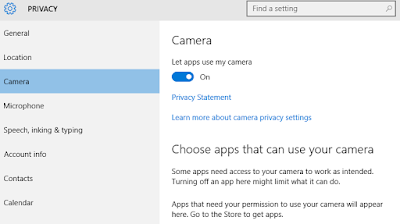
Once you've exported these in, take a Windows 10 machine with all of the default, intrusive settings turned on, as shown in the example screenshot below where the Camera is allowed to access your location
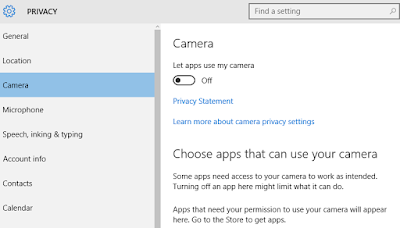
and then import in the settings we've configured, and then have a look at the same settings again once you've logged out and back in again
You should find that all of the settings are now turned off, and that privacy is now as God intended :-)
Finally, if you're not using OneDrive, then it would be a good idea to disable it as in this previous article
5. System services
If you're slightly more paranoid, you can actually wax a couple of system services to help with privacy.
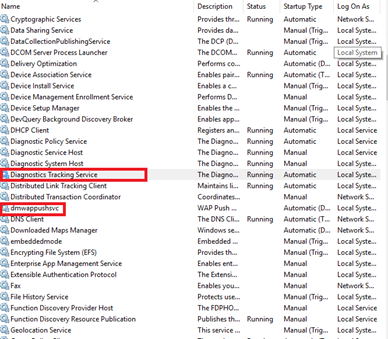
The services we're concerned with are shown in the diagram below, both these should ideally be Disabled (although test thoroughly before you deploy)
In my experience, there's nothing that has broken when disabling these services, but don't be tempted just to take my word for it!
Update 22 Nov 2015 - the sneaky little gits at Microsoft have, via update 1511 for Windows 10, renamed the Diagnostics Tracking Service to the much-less-nasty-sounding Connected User Experiences and Telemetry Service. So disable this service too. Nothing like using Windows Update as a new point to enable data slurping, eh?
6. Hosts file blocking (more tinfoil)
Now we're starting to descend into the section for those of you with considerably larger pieces of tinfoil headwear. Many have been out Wiresharking their Windows 10 installations, and there are a whole host of Microsoft web addresses that (apparently) the operating system likes to talk to. You can use a hosts file in %WINDIR%\system32\drivers\etc to block access to these web addresses, if you're so inclined. The list of addresses is below, along with the IP addresses to blackhole them
I think that you'd have to be very careful with this, particularly in an environment where you have any reliance on Office365, Azure or any other Microsoft online services. Personally I wouldn't go this far, but the choice is yours :-)
7. Firewall blocks (for the batshit paranoid)
If you are really out there with the conspiracy theorists, there are (allegedly) a couple of Microsoft web addresses that use a dll in the operating system (%WINDIR%\system32\dnsapi.dll, apparently) to bypass the Windows hosts file and communicate directly.
There are a number of sites that will report various addresses for this behaviour, but your only choice would be to block them at the firewall. You'd have to investigate them yourselves if you wanted to do this, but most of them tend to be of the format
*.vortex-win.data.microsoft.com
Again, loving the choice of words - vortex sums up a lot of my thoughts on Windows 10 data mining pretty well.
Summary
Test thoroughly, but if you use the settings from the first five sections we covered, I think you should be quite OK. Disabling the services is quite reasonable in an enterprise environment - but the use of thehosts file and the firewall blocking is probably a bit much, in my opinion. However - whatever you use, make sure you test it!
More on my thoughts on Windows 10 and what it means for UEM in general later this week. In the meantime - happy privacy! :-)
I had to use AppSense for the tooling because of the requirement for a delay after logon before importing the settings, so traditional Group Policy/scripted methods will probably be unsuitable here, although the more skilled scripters among you should be able to adapt. Ideally, though, to enforce these privacy settings and save yourselves from having your policies overwritten by the default profile, a high-end UEM solution of some sort is required.
Spaying your Windows 10 instance
1. Universal Apps
First step is to ensure that your Windows 10 is as unintrusive as is humanly possible, by removing apps and features that you don't require.
Given how bad the feedback on Universal Apps has been so far, I'd be in the mood to remove all of them (except Edge maybe - my users seem happy about that, although given they're coming from IE7 most anything is an improvement). If you're on LTSB most of the Universal Apps are removed anyway, but any other servicing branch and you'll have all of the horrid guff hanging from your Start Menu. They also love to talk back to Microsoft!
Get rid of most of these (with the exceptions of the annoying Contact Support and Windows Feedback) by getting down-and-dirty with this bit of handy PowerShell (you will need to run it with admin privileges)
Get-AppxPackage -AllUsers | Remove-AppxPackage
and you should see something like this (you can ignore all of the errors - they're just stuff that, for whatever reason, can't be removed)
You can also use this command
Get-AppXProvisionedPackage -online | Remove-AppxProvisionedPackage -online
if you want to remove applications in the image rather than after the operating system has been loaded.
Cortana should be removed as part of this process also.
2. Web search from desktop
You can get rid of web search and avoid routing everything you search for through Bing by using some Group Policy Objects. Rather annoyingly (and not very surprisingly these days), they are computer GPOs rather than user ones. Configure the settings in Computer Configuration | Admin Templates | Windows Components | Search as below (these settings are included in my example configuration)
3. Telemetry
If you're using the Enterprise version of Windows 10, you can disable Telemetry through GPO as well. If you're not on Enterprise - well, you can reduce it somewhat, but not kill it. With this in mind, I'd recommend everyone use Enterprise where possible and setting the policy to Off(shown below - also included in the example configuration)
If you're not on Enterprise all you can do is go for Basic as the setting. The differences between Basic, Enhanced and Fullare known only to Microsoft (Off is supposed to send nothing at all, but I don't believe that for a second), but they do insinuate that Off or Basic will "degrade certain experiences on the device". It may well degrade the experience of being spied on and monitored, but I haven't noticed anything keel over and die since I deployed this to my users in Off mode.
Apparently (though I can't confirm), if you're not on Enterprise you can trick Windows into disabling telemetry by creating the following Registry value
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DataCollection
DWORD AllowTelemetry Value 0
although I'm fairly sure if this works, Microsoft will plug the hole as soon as possible.
4. Detailed privacy settings
At build time there's a bunch of stuff you can do to turn off most of the nosier features of Windows 10. You can also do this post-build, but controlling them centrally is a little more challenging. I've put together a set of policy objects and preferences (available in AppSense Environment Manager format), which will need to be imported onto a Windows 10 machine with a copy of the Windows 10 ADMX files running the required EM Console.
You will need to check and test these to ensure that they aren't conflicting with existing policies. A lot of them I've put in as Computer GPOs because they are restricted to that scope, but there may be a few available as User settings as well. The Registry values, for settings that don't have policies attached, are all set in the user context.
For the Contacts settings, the Registry key contains a SID - S-1-15-2-155514346-2573954481-755741238-1654018636-1233331829-3075935687-2861478708 - which does not resolve to anything on my test domain or test machines. You actually need to use this SID hard-coded as part of the Registry path to get the Contacts settings successfully blocked. Not sure where this has come from.
There is also a distressing tendency for the default profile creation to overwrite a lot of the Registry settings we have configured here (well, no-one said it was going to be easy!) To get around this, we will have to resurrect the Post-Logon Trigger that was supposed to be replaced by Desktop Created in AppSense (not the first time we've done this in the post-Windows 7 world), to import our settings in after Microsoft's default profile has done its damage. Big feature request to AppSense - give us a native "Delayed Trigger", customizable to a specific time frame after logon (Scense, one of your competitors, can do this natively), or even something like a "Refresh Trigger" (again, Scense has it) that runs at a pre-determined interval. Since Windows 8 and 10 came along the Desktop Created trigger runs too early to head off some of Microsoft's more questionable programming choices - please save us from using the PowerShell method and make it native in a new release!
The Environment Manager config is available here, and contains the necessary settings for the Post-Logon Trigger as well. What you will notice is there are some fabulous names for the Registry values we're using, and they make a little bit of a mockery of Microsoft's benign intentions for your data - HarvestContacts and RestrictImplicitTextCollection being my personal favourites.
You may actually need to tweak the delay in the Post-Logon Trigger dependent on your profile, I had to increase from 2000ms to 8000ms in one case. In the PowerShell that creates the .cs file (see the attached config), increase the sleep timeout as necessary to get it to work.
Once you've exported these in, take a Windows 10 machine with all of the default, intrusive settings turned on, as shown in the example screenshot below where the Camera is allowed to access your location
and then import in the settings we've configured, and then have a look at the same settings again once you've logged out and back in again
You should find that all of the settings are now turned off, and that privacy is now as God intended :-)
Finally, if you're not using OneDrive, then it would be a good idea to disable it as in this previous article
5. System services
If you're slightly more paranoid, you can actually wax a couple of system services to help with privacy.
The services we're concerned with are shown in the diagram below, both these should ideally be Disabled (although test thoroughly before you deploy)
In my experience, there's nothing that has broken when disabling these services, but don't be tempted just to take my word for it!
Update 22 Nov 2015 - the sneaky little gits at Microsoft have, via update 1511 for Windows 10, renamed the Diagnostics Tracking Service to the much-less-nasty-sounding Connected User Experiences and Telemetry Service. So disable this service too. Nothing like using Windows Update as a new point to enable data slurping, eh?
6. Hosts file blocking (more tinfoil)
Now we're starting to descend into the section for those of you with considerably larger pieces of tinfoil headwear. Many have been out Wiresharking their Windows 10 installations, and there are a whole host of Microsoft web addresses that (apparently) the operating system likes to talk to. You can use a hosts file in %WINDIR%\system32\drivers\etc to block access to these web addresses, if you're so inclined. The list of addresses is below, along with the IP addresses to blackhole them
0.0.0.0 vortex.data.microsoft.com
0.0.0.0 telecommand.telemetry.microsoft.com
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net
0.0.0.0 oca.telemetry.microsoft.com
0..0.0.0 oca.telemetry.microsoft.com.nsatc.net
0.0.0.0 sqm.telemetry.microsoft.com
0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net
0.0.0.0 watson.telemetry.microsoft.com
0.0.0.0 watson.telemetry.microsoft.com.nsatc.net
0.0.0.0 redir.metaservices.microsoft.com
0.0.0.0 choice.microsoft.com
0.0.0.0 choice.microsoft.com.nsatc.net
0.0.0.0 df.telemetry.microsoft.com
0.0.0.0 reports.wes.df.telemetry.microsoft.com
0.0.0.0 wes.df.telemetry.microsoft.com
0.0.0.0 services.wes.df.telemetry.microsoft.com
0.0.0.0 sqm.df.telemetry.microsoft.com
0.0.0.0 telemetry.microsoft.com
0.0.0.0 watson.ppe.telemetry.microsoft.com
0.0.0.0 telemetry.appex.bing.net
0.0.0.0 telemetry.urs.microsoft.com
0.0.0.0 telemetry.appex.bing.net:443
0.0.0.0 settings-sandbox.data.microsoft.com
0.0.0.0 vortex-sandbox.data.microsoft.com
0.0.0.0 survey.watson.microsoft.com
0.0.0.0 watson.live.com
0.0.0.0 watson.microsoft.com
0.0.0.0 statsfe2.ws.microsoft.com
0.0.0.0 corpext.msitadfs.glbdns2.microsoft.com
0.0.0.0 compatexchange.cloudapp.net
0.0.0.0 cs1.wpc.v0cdn.net
0.0.0.0 a-0001.a-msedge.net
0.0.0.0 statsfe2.update.microsoft.com.akadns.net
0.0.0.0 diagnostics.support.microsoft.com
0.0.0.0 corp.sts.microsoft.com
0.0.0.0 statsfe1.ws.microsoft.com
0.0.0.0 pre.footprintpredict.com
0.0.0.0 i1.services.social.microsoft.com
0.0.0.0 i1.services.social.microsoft.com.nsatc.net
0.0.0.0 feedback.windows.com
0.0.0.0 feedback.microsoft-hohm.com
0.0.0.0 feedback.search.microsoft.com
0.0.0.0 bingads.microsoft.com
0.0.0.0 www.bingads.microsoft.com
127.0.0.1 apps.microsoft.com
127.0.0.1 www.apps.microsoft.com
I think that you'd have to be very careful with this, particularly in an environment where you have any reliance on Office365, Azure or any other Microsoft online services. Personally I wouldn't go this far, but the choice is yours :-)
7. Firewall blocks (for the batshit paranoid)
If you are really out there with the conspiracy theorists, there are (allegedly) a couple of Microsoft web addresses that use a dll in the operating system (%WINDIR%\system32\dnsapi.dll, apparently) to bypass the Windows hosts file and communicate directly.
There are a number of sites that will report various addresses for this behaviour, but your only choice would be to block them at the firewall. You'd have to investigate them yourselves if you wanted to do this, but most of them tend to be of the format
*.vortex-win.data.microsoft.com
Again, loving the choice of words - vortex sums up a lot of my thoughts on Windows 10 data mining pretty well.
Summary
Test thoroughly, but if you use the settings from the first five sections we covered, I think you should be quite OK. Disabling the services is quite reasonable in an enterprise environment - but the use of thehosts file and the firewall blocking is probably a bit much, in my opinion. However - whatever you use, make sure you test it!
More on my thoughts on Windows 10 and what it means for UEM in general later this week. In the meantime - happy privacy! :-)